First enumeration with nmap
┌──(n16hth4wk👽n16hth4wk-sec)-[~/Documents/PGP/USV2017]
└─$ cat normal.tcp
# Nmap 7.93 scan initiated Mon Mar 6 19:29:43 2023 as: nmap -sC -sV -oN normal.tcp -p 21,22,80,4369,5222,5269,5280,15020,45707 -Pn 192.168.117.19
Nmap scan report for 192.168.117.19
Host is up (0.15s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5b
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
| ssh-hostkey:
| 256 b82961bbf18cc464ddf50ea0a22ffdaa (ECDSA)
|_ 256 2b7e351042ca082066418880a04f02e6 (ED25519)
80/tcp open http Apache httpd
|_http-server-header: Apache
|_http-title: Site doesn't have a title (text/html).
4369/tcp open epmd Erlang Port Mapper Daemon
| epmd-info:
| epmd_port: 4369
| nodes:
|_ ejabberd: 45707
5222/tcp open jabber ejabberd (Protocol 1.0)
| xmpp-info:
| STARTTLS Failed
| info:
| xmpp:
| lang: en
| server name: localhost
| version: 1.0
| compression_methods:
| capabilities:
| errors:
| host-unknown
| host-unknown
| (timeout)
| unknown:
| features:
| auth_mechanisms:
|_ stream_id: 3904735158632223365
5269/tcp open jabber ejabberd
| xmpp-info:
| Ignores server name
| info:
| xmpp:
| version: 1.0
| capabilities:
| pre_tls:
| xmpp:
| capabilities:
| features:
| TLS
| post_tls:
| xmpp:
|_ capabilities:
5280/tcp open ssl/xmpp-bosh?
| ssl-cert: Subject: commonName=ejabberd/organizationName=stl.int
| Not valid before: 2017-10-23T20:50:49
|_Not valid after: 2018-10-23T20:50:49
|_ssl-date: TLS randomness does not represent time
15020/tcp open http Apache httpd
|_http-title: 400 Bad Request
|_http-server-header: Apache
45707/tcp open unknown
Service Info: Host: localhost; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Mar 6 19:32:16 2023 -- 1 IP address (1 host up) scanned in 153.52 seconds
cool we know what ports are open.
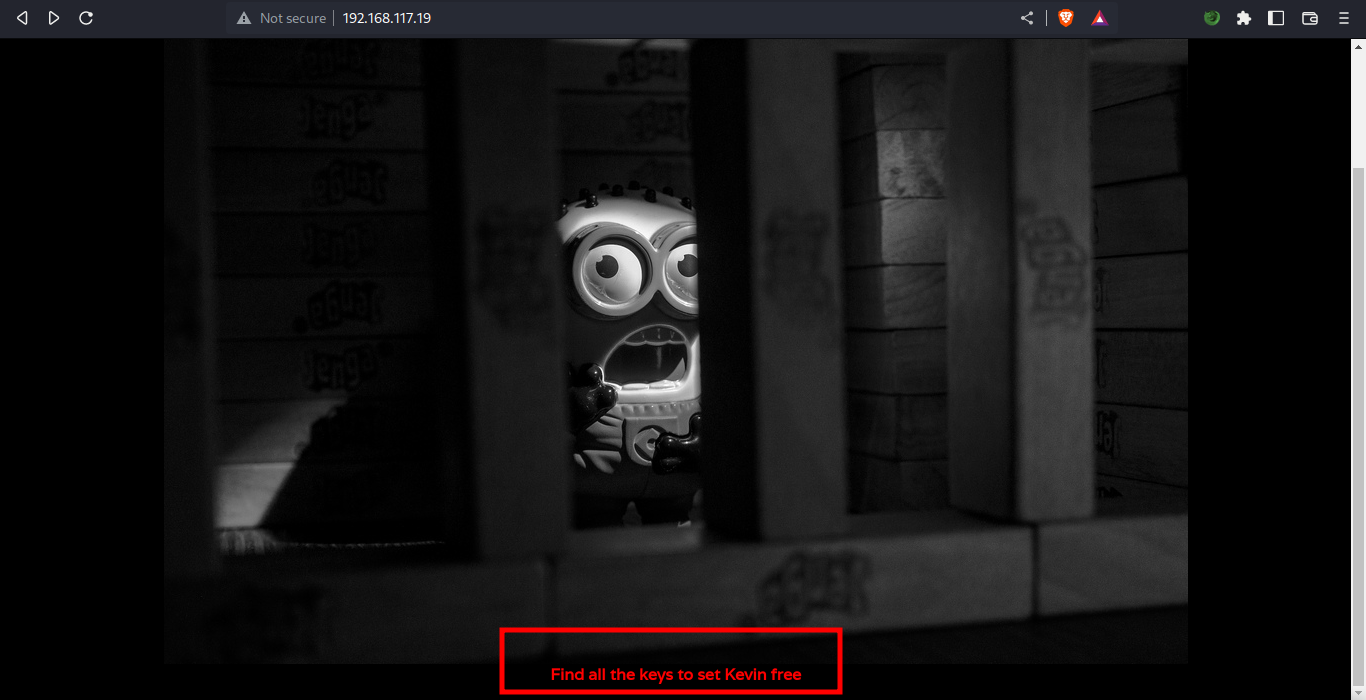
noticed a webserver running on port 80, opening it on a browser we got directed to an homepage with a character in jail.